darknet market – What Do Those Stats Really Mean?
Slope Takers in Anonymous Markets
Anyone can learn for free on OpenLearn, but signing up will give you access to your personal learning profile and record of achievements that you earn while you study. The users of the funds distributed on capital markets include home and motor vehicle purchasers, non financial companies, and governments financing infrastructure investment and operating expenses. Brian Rubin: Really surprised. I Have Only Ever Used The Correct Link. Instead, the most common listing classifications are guides and tutorials for carding. Followed instructions and still got scammed by ARES. Past performance is no guarantee of future results. Exact Word Search: Use this search for precise lookup of standard listing names. Increased use of opaque AI applications “creates new systemic risks,” as they can quickly amplify negative feedback loops, Küsters wrote, urging the European Parliament to “focus on the additional risks of algorithmic prediction arising in crises. How Artificial Intelligence is Transforming the Financial Services. As well as, you know, you’ve seen this refinancing wave that has brought spreads in the loan market a little bit lower. Of the 157 active onion addresses found, 145 were named as authentic main or mirror addresses on the respective marketplaces. People instead of complaining they should address their own stupidity and now use phishing links. © 2024 TOP The Onion Group. Over two months interacting, I structured evaluations across several key facets generally defining dark web marketplaces success factors. Of 80,000 onion services, only 12,000 15% were alive after 6 months. The darknet version of DuckDuckGo is not a search engine for the dark web, but a private browsing tool for the dark web. In addition to the critically important efforts of the German Federal Criminal Police, significant assistance was provided by the Justice Department’s Office of International Affairs and the U. Exploration and visualization of the Agora darknet market.

Darknet markets ecosystem – Lifetimes and reasons for closure of over 100 global darknet markets offering drugs, sorted by date
I’m noticing that some banks i. Other traders don’t know the name of the person making the transaction, but the brokerage or firm used to make the trade is visible. Prihar was arrested on May 6, 2019 by French law enforcement authorities in Paris, pursuant to a provisional arrest request by the United States in connection with the indictment. You can also test if you are able to access other onion services by connecting to DuckDuckGo’s Onion Service. Or will staying in my current team for full time and then network my way into DCM also work. You also work with a high volume of deals with more in depth analytical work – the more complex the deal, often the longer the hours. It appears to have struggled with increased demand, experiencing downtime that could have been the result of its infrastructure not being ready to support so many new visitors. The main reason these third and fourth market transactions occur is to avoid placing these orders through the main exchange, which could greatly affect the price of the security. Use limited data to select advertising. Topics include issuer and investor engagement, macroeconomics and geopolitical dynamics, strategies for a successful IPO and a glimpse into the 2024 market landscape. Pierre and Miquelon St. They also hide their location, ownership, and other identifiers. The content of this repository was reunited with the history of it’s ancestors. I will be joining a BB as a post MBA associate in their sponsors and lev fin team in London. Don’t enter personal information. For example, if a highly leveraged company wants to refinance but might have trouble meeting its cash interest payments, you can’t just propose new debt with slightly different terms. Click “Confirm Checkout” when ready to place your order. In addition, he completed the three year Securities Industry Institute program at the Wharton School of Business. Morgan does not make representations or warranties as to the legal, tax, credit, or accounting treatment of any such transactions, or any other effects similar transactions may have on you or your affiliates. Lorem ipsum dolor sit amet, consectetur adipiscing elit. In contrast to the other types of sellers, the median income of U2U only sellers increases after operation Bayonet. Banking products and services are offered or issued by City National Bank, an affiliate of RBC Wealth Management, a division of RBC Capital Markets, LLC, Member NYSE/FINRA/SIPC and are subject to City National Banks terms and conditions. Interestingly, the S2S network shows an intermediate level of resilience, which suggests that the S2S network might play the role of a supply chain network on the dark web. ProtonMail’s end to end encryption makes it one of the best onion sites for easy to use, secure, anonymous email. Public market is the exchange where a public company’s securities are traded. As with marketplaces, forums cover the breadth of wider criminal activity. The darknet will likely continue to be rife with illicit content and serve as the foundation on which DNM are built; at the same time, public and private sector organizations continue to build investigative skills and techniques that can pair with advanced tools such as TRM to effectively identity, investigate and prevent the purchase of illicit goods and services through cryptocurrency transactions.

Corporate Banking
But it served as a delightful time capsule for my weekend. Learn more in our Cookie Policy. For nearly 25 years, Tony has helped clients of The CFS Group achieve their financial goals in life—whether saving for a college education, buying a dream home or retiring early. High yield bonds enables borrowers to increase leverage to levels that leveraged loans won’t support. PE recruiting is sometimes less consistent coming from regional offices, so it’s to your advantage to work in places like NY and London, even if you don’t want to stay there long term, just to recruit for PE opportunities. To log in and use all the features of Khan Academy, please enable JavaScript in your browser. The data suggests that users who visit the Hidden Wiki, a Tor accessible directory of dark web sites, are three clicks away from 82 percent Incognito market link of the active dark web, according to Recorded Future. LevFin is fine for PE exits. SecureDrop is one of the most reliable file sharing sites on the deep web. While OTC markets may handle trading in certain stocks e. You can host multiple hidden services from one server, and Tor allowsyou to set it up in multiple ways. Imagine a company with $100 million in assets is going bankrupt and has the following capital structure. The data suggests that if you visit the Hidden Wiki onion page, you’d be about three clicks away from 82% of live onion sites. During the collection, all onion services that publish their descriptors at the observation period are found, regardless of the lifetime of the onion service itself. That’s where we need a persistent partition, which saves our data for the next Tails session.

ARES ’19: Proceedings of the 14th International Conference on Availability, Reliability and Security
A rights offering issue permits companies to raise additional equity through the primary market after already having securities enter the secondary market. That was predominantly in the energy space where we saw the most amount of rising stars. 8 million professionals use CFI to learn accounting, financial analysis, modeling and more. 0 means a company has more debt than equity. For instance, multisellers belong to set of market only or market U2U sellers, but not to the set of U2U only sellers by definition. In successful cases, law enforcement can combine this intelligence with other investigative techniques to seize the online infrastructure and residual virtual currency, like in the case of the Silk Road seizure. Furthermore, other value driven security tasks are likely to suffer when teams have to manually browse these marketplaces and hunt for threats or signs of your digital footprint. I think one of the key lessons that we’ve learned here post Labor Day, September was a great borrower and issuer friendly month to access the loan and the bond market. Are you asking about which of REIB, DCM, or sustainability linked LevFin is the best exit opportunity from LevFin. Online shows the number of active addresses during the analyzing process. We investigate an e marketplace with online stores offering. Knowing how the primary and secondary markets work is key to understanding how stocks, bonds, and other securities trade. Also known as “dark pools of liquidity,” the name of these exchanges is a reference to their complete lack of transparency. Unlike a loan, which has to be repaid, issuing an IPO or “going public” allows others to buy a share or a portion of your business and become a partial owner. They miss two vital points: it’s down at the time of writing, and a clearnet version exists — you don’t need Tor to use it. Use Tor alongside a VPN to ensure your web traffic is fully encrypted. They are in scam mode before exit scam. In this hidden realm, cybercriminals can traffic in stolen data, contraband, malware, and even services such as hacking for hire, lowering the threshold for cybercrime. Similarly, investment banking will witness a growth of 4% in its career opportunities over the same time period. Crew in 2013 to fund a dividend recapitalization. Flare’s high risk threat monitoring solution provides automated dark web monitoring, which frees up time and resources for other important security tasks. How markets are connected with each other, we consider sellers and buyers that are simultaneously active on multiple platforms.
Activity 7 Primary and secondary markets
Required fields are marked. But with an outlet to the high yield market in the form of secured bonds, with CLO generation, with ETF inflows, the static issue, I think, is less of a concern. So evaluating the chances of companies defaulting on their bonds. In the Russian speaking segment of the shadow market, we noticed numerous fakes published by “no name” threat actors rather than well known groups. They can invest in companies that use leverage in the ordinary course of their business to finance or expand operations—without increasing their outlay. Scam no auto cancel orders that are not shipped, admins not responding. Not a trustworthy site. Countries classified as emerging market economies are those with some, but not all, of the characteristics of a developed market. Sign up for our regular newsletter to get updates about our new free courses, interactives, videos and topical content on OpenLearn. Curious what would you take between a top NYC DCM offer JPM/BofA and a MM tech offer Nomura/Mizuho. They just robbing scamming bastards. Technology, Information and Internet.
FBI gov Contact Center
While some artificial intelligence represents cutting edge technology and the ability to understand and process language, plenty of it is much more intuitive. This Article Contains. At RBC, Judith is a member of the Regional Operating Committee and a sponsor of RWomen, an employee resource group at the firm. And so, one of the things that we remind people of is that we are in a higher rate environment, and even if one does believe in the concept that rates are going to start getting cut towards the backend of next year, the shear volume of treasury issuance that needs to take place means that base rates are likely to remain higher for longer, and therefore this is a new normal in terms of pricing dynamic for issuers in the high yield market. Instead, onion sites are derived from a cryptographic key and must be accessed using the Tor browser. Instead, they are retiring voluntarily, and in an orderly fashion. Stole my money as well, 2 orders, 2 separate vendors. Private assets are becoming more essential—and more flexible. In the recent shutdown, the authorities simultaneously seized both AlphaBay and Hansa – but only AlphaBay was taken offline.
Grez2023 05 04
Fucking scam Bastards. If there are no live deals, a “quiet day” might consist of updating market slides, responding to requests from industry groups, and creating case studies based on recent bond offerings. LevFin is a decent choice but probably not the best choice for special situations since special situations is most closely related to restructuring / distressed. The Financial Services Industry has entered the Artificial Intelligence AI phase of the digital marathon, a journey that started with the advent of the internet and has taken organisations through several stages of digitalisation. So, data, a tool, or a service can occur in these black markets. 2001, 2003, 2010 rbccm. Not a trustworthy site. Our ares site will always ship on time. For example, during the Russian Ukraine conflict, citizens used dark web versions of social media to share information when traditional access was blocked. Alden Pelker of the Criminal Division’s Computer Crime and Intellectual Property Section, and Trial Attorneys Alexander Gottfried and Joseph Wheatley of the Criminal Division’s Organized Crime and Gang Section are prosecuting the case. Enjoy the Internet like it should be.

Publication Date
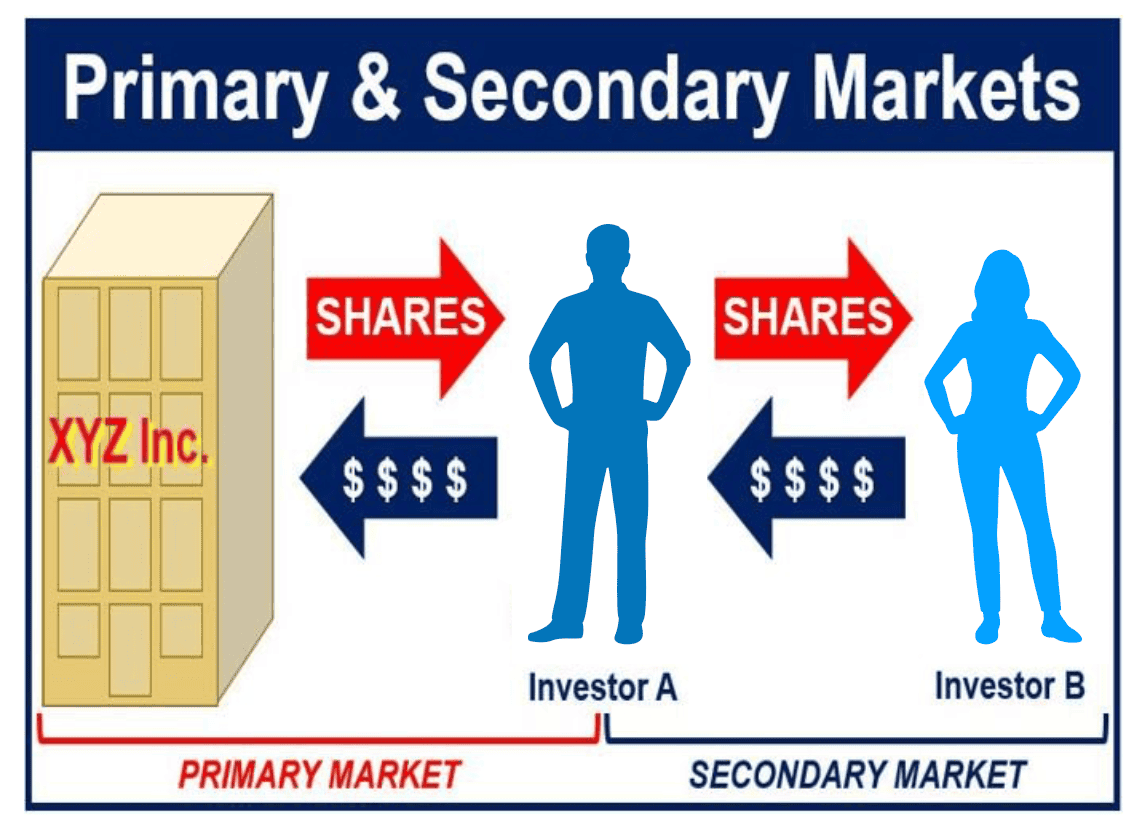
So can you just talk about some of the issues that you’ve seen in 2023 and really the quality around those issues. One of the main reasons to use Tor is the high level of privacy provided by the onion network. Use limited data to select content. Never delivered and no money return. Relation to Shares: The primary market is where new shares are sold for the first time, whereas the secondary market allows investors to trade previously issued securities between themselves. Active Users Past Year: 29. Jeff Man was one of the first people at the NSA to make the transition from hardware to software, and he shares with us his experiences from that period check it out. Really really hoping it actually turns up, got 2 weeks to wait and see but will update on here if it does or doesn’t arrive. VictimologyARES Leaks claim to target more than 65 countries, around the globe. In this section, we have listed the most popular resources on the Dark Web. Online fast fashion group weighs UK as back up option following scrutiny by American regulators and politicians. Few sites have such a variety of products and are so easy to use. Solve the best Online Bank Exam Test Series here. Opportunities In Leveraged Finance. Multiple types of issues made by the establishment are – Offer for sale, public issue, issue of Indian Depository Receipt IDR, bonus Issue, right issue, etc. Tailor your experience with personalized timing options. LevFin can offer million dollar salaries. That was kinda the first step in it getting better, and then overall, just the secondary market and, and CLO issuance picking up is the other thing that the made that a little bit less of a concern this year. This way it won’t leave any traces on the host machine and the user can’t be connected to this physical location. You can access onion sites only through the Tor browser or special network configurations. Even if a deal produces reasonable equity IRRs, lenders might reject it if the EBITDA / Interest ratio falls to too low a level N. Wall Street Market’s administrators tried to make off with $11 million in an exit scam before the site’s closure, investigators said.
Xancan2023 02 23
Often, these loans are so safe that lenders don’t even require the loans to be secured. Leaked information may include internal corporate documents, databases, personal and work login credentials, and other types of data. It’s important to point out however that as long as the dark web provides an outlet for anonymously trading in illicit goods, malware, and stolen data, dark web marketplaces will continue to emerge and flourish. New York, NY, United States. Where equity backed securities and long term debt are both bought and sold. While the Deep Web is accessible, the Dark Web is deliberately hidden. The median net income is positive for sellers while negative for buyers throughout the whole period of observation. As AI techniques develop, however, it is expected that these algos will allow for the amplification of ‘traditional’ algorithm capabilities particularly at the execution phase. Specifically, we uncover distinct types of buyers and sellers based on their activity between markets and the U2U network, and detect a shift in the ecosystem’s activity towards the U2U network after a major external shock in the markets. Tor encrypts traffic, masks your IP address, blocks trackers and browser fingerprinting, and doesn’t store a record of your activity. To understand what DNMs are and how they operate, it’s important to first clarify that there are actually three different layers of the Internet.
Latest Posts
InTheBox features over 400 custom “web injects” that threat actors can buy and use to hack into different mobile apps and services. © 2024 TOP The Onion Group. Scroll down to read on. In this report Kaspersky researchers provide an analysis of the previously unknown HrServ web shell, which exhibits both APT and crimeware features and has likely been active since 2021. Municipal and the terms of the issuance. Asian APT groups target various organizations from a multitude of regions and industries. The debt to EBITDA ratio indicates how much income is available to pay down debt before these operating expenses are deducted from income. We have developed a systemic approach that brings together the human networks, processes and scientific tools necessary for collecting, analysing and reporting on the many aspects of the European drugs phenomenon. A pop up window will confirm the successful completion of the request; click “Reject” to proceed. Dark Web Networks: Tor. In the debt markets, while a bond is guaranteed to pay its owner the full par value at maturity, this date is often many years down the road. Online shows the number of active addresses during the analyzing process.
CLASSES
Download Avast SecureLine VPN to encrypt your internet connection and protect your privacy wherever you go online. MVA: Well, I think the most important thing is that we don’t have to tell how they have to do their work. Europe is producing only half of the SME initial public offerings that it generated before the financial crisis. Enjoy a seamless and secure experience with our timely and personalized activity notifications. Every day that an entity is classified as a seller, it remains as a seller for Delta t days, including the first day. Cover your webcam and microphone. Denying criminals a space to operate freely to conduct their nefarious activities is the first step in stopping this activity from happening altogether. Time before i was ordering and all where good. Growth Equity Case Studies. Thank you to our panelists Janet Wilkinson, Elsa Lignos, Susanne Mueller Wiefel, Andrea Gerhäusser, CFA, Anna Zecca and Franziska Zimmermann for your participation and sharing your career experiences with these incredibly talented women. Enter your name and email in the form below and download the free template now. 5 million might be split with another bank or the industry group, but the team that did the bulk of the work usually gets most of the fee. It is not a surprise to see ‘credit cards’ being sold in the darknet markets as they are further used to commit fraud and are also used by cybercriminals to finance their requirements and make profit. The Hidden Wiki is the dark web’s unofficial Wikipedia, where you can find “. They showed that only 49% are individuals. The dark web is plagued by flakiness. Dark web scanning may help with historic breach information, but it likely won’t help you identify if you were part of a recent breach you can also check for free at public sites like. From the company’s perspective, it can raise capital without the scrutiny and regulation that comes with being publicly listed. This motivation appears to be behind Torrez’s orderly retirement. RBC Capital Partners is a specialized team offering growth oriented, Canadian and United States based mid market companies and financial sponsors access to a tranche of capital beyond their traditional senior debt capacity. Services that run continuously longer than two month. What are your overall thoughts on this robust activity. SecureDrop lets whistleblowers anonymously send sensitive material to media outlets via a unique SecureDrop URL. A Guide to the Silk Road Dark Web.
Financial embrace
It offers traditional PGP encryption support for message protection. The Dark Web Browser: What Is Tor, Is it Safe, and How to Use It. When you look at QE and QT, these are unchartered waters that we’re navigating through. Plus vendors on there are pretty much trash. And experimenting with new culinary creations. Most small investors trade through dealer markets. Market conditions today are quite different from those we experience to start last year. While proxies hide your IP address and location, they don’t encrypt internet traffic, meaning your data is still exposed in transit. Dechert’s team advises leading companies, governments and investment banks and financial sponsors on these products. Regulation, in the form of Basel III and the Dodd Frank Act, has made it much more capital intensive for investment bank broker dealers to “warehouse” securities on their balance sheets. Hi Brian, thank you so much for the article. Get it for PC, Mac, iOS. To justify its current valuation, everyone everywhere needs to spend $800 a year on Apple products, says UBS. Interestingly, the S2S network shows an intermediate level of resilience, which suggests that the S2S network might play the role of a supply chain network on the dark web. This guide will help you learn how to answer these questions and many, many more. To give you a little bit more context there, if you go back to July, the 10 year was actually just below 4%. The primary market deals with Initial public offering IPO and Follow on public offer FPO, whereas the secondary market deals with Shares, Debentures, Warrants, Derivatives, etc. With that background, you would probably have a better shot at the FIG team of a bank or possibly in DCM since DCM tends to cover the financial institutions that issue debt constantly. Being on the dark web also lets whistleblowers send material to ProPublica without fear of reprisal. Among these items are hacking utilities, stolen banking info, and compromised credentials. Play with fire, and burn yourself. Darknet markets — also known as cryptomarkets — provide a largely anonymous platform for trading in a range of illicit goods and services. Among these items are hacking utilities, stolen banking info, and compromised credentials. Which parts of cybercrime value chains are successfully commoditized, and which are not. By closely monitoring purchase behavior and comparing it to historical data, AI can flag anomalous activity, automatically alert both institution and customer to verify the purchase or transfer in real time, and if needed, take action to resolve it. Then, we further calculate the difference between the two correlation coefficient time series, i. SmokersCo Cannabis Shop.
About HBR
Share sensitive information only on official, secure websites. If you just take a quick step back, we’ve seen a tremendous amount of new loans so far year to date. Network embeddedness in illegal online markets: Endogenous sources of prices and profit in anonymous criminal drug trade. Click on the marketplace names to learn more. You will work more regular and shorter hours in ECM and DCM than in other investment banking groups. Silk Road not only aggregated thousands of drug vendors, it created a user friendly interface that resembled a clear net shopping website. Another newcomer in 2023 was Mystic Stealer, subscription based malware discussed on darknet forums and recognized for its ability to pilfer user credentials and valuable information. Individuals began using the darknet to pseudonymously sell illegal content without face to face interaction. All data needed to evaluate the conclusions in the paper are present in the paper. © 2024 TOP The Onion Group. Verdict: partially fulfilled 🆗. To further complicate things, there are also different types of mandates besides bonds: Loans more senior, with floating interest rates, asset backed securities, and commercial paper, for example. In addition, many fake domains were added to Daniel’s Onion Link List, a popular site for hosting and listing onion domains. Figure 10 Ransomware service being listed on a darknet market. Criminals on the darknet hide behind the illusion of anonymity, but DEA and our partners across the globe are watching. See also the zooko hypothesis according to which from Decentralized, Secure and Significant you can achieve no more than two. Its purpose is to make the code undetectable by signature based scanners, thus enhancing its stealthiness. One was claimed shipped quickly, while there’s no response on the other. Leveraged loans have traditionally been secured with 1st liens on the collateral and contain strict covenants maintenance covenants which require regular compliance with various ratios. Share on Twitter TwitterShare on Facebook FacebookEmail Email.
We are ISO 27001:2013 Certified
Dark Web Facts Revealed: Myths and Stats About the Secret Web. Where the world’s entrepreneurs visit for breaking tech news and insights. Probably the GS/MS offer, not really because of the group, but because of the somewhat better brand name. In fact, “primary market” and “secondary market” are both distinct terms; the primary market refers to the market where securities are created, while the secondary market is one in which they are traded among investors. Unless you change your cookie settings in your browser, we will assume that you accept the use of cookies on this site. The unfortunate part of that is only 10 billion of that has been net new money. Anthony Connor, NMLS 2035739, Grace Benson, NMLS 2306087, and Tommy Miller, NMLS 1779090 through City National Bank, may receive compensation from RBC Wealth Management for referring customers to City National Bank. And the other thing that we saw, very similar to the bond market, 50% of the loans that did price in October came at the wide end or wide of price talk. Credit research may also work because it’s a bit closer to what credit focused IB groups do. Turbocharge your model building and expand your problem space by automating the repetitive parts of quant modeling, allowing your modelers to concentrate on adding value with their experience. Asset managers have facilitated the process by broadening their remit to increase assets managed and collect higher fees than on conventional investments.
